3 minute read
I hadn’t played SharifCTF before, but these guys put on a good competition.
Unfortunately I had other commitments, but I managed to spend a little bit of time looking at some of the challenges.
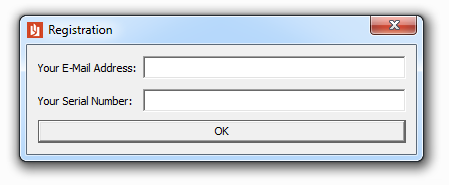
dMd was a reverse engineering challenge worth 50 points. A binary was provided with the description:
Flag is : The valid input.
file told me that the binary was an x86-64 ELF, so I threw it at my Fedora install and pulled up the disassembly in IDA.