Posted: 22 Nov 2017 by Codehead
18 minute read
After completing the video lectures of the Security Tube Linux 64 bit Assembler Expert course (SLAE64), a series of assessments must be completed to gain certification. This is the fifth assignment; analyse 3 payloads generated by the Metasploit msfvenom tool.
msfvenom is a replacement for msfpayload and msfencode tools. It combines their functionality into a single application. The available payloads specifically for x64 Linux are quite limited:
root@kali:~# msfvenom -l | grep linux/x64
linux/x64/exec Execute an arbitrary command
linux/x64/meterpreter/bind_tcp Inject the mettle server payload (staged). Listen for a connection
linux/x64/meterpreter/reverse_tcp Inject the mettle server payload (staged). Connect back to the attacker
linux/x64/meterpreter_reverse_http Run the Meterpreter / Mettle server payload (stageless)
linux/x64/meterpreter_reverse_https Run the Meterpreter / Mettle server payload (stageless)
linux/x64/meterpreter_reverse_tcp Run the Meterpreter / Mettle server payload (stageless)
linux/x64/shell/bind_tcp Spawn a command shell (staged). Listen for a connection
linux/x64/shell/reverse_tcp Spawn a command shell (staged). Connect back to the attacker
linux/x64/shell_bind_tcp Listen for a connection and spawn a command shell
linux/x64/shell_bind_tcp_random_port Listen for a connection in a random port and spawn a command shell.
Use nmap to discover the open port: 'nmap -sS target -p-'.
linux/x64/shell_find_port Spawn a shell on an established connection
linux/x64/shell_reverse_tcp Connect back to attacker and spawn a command shell
Posted: 9 Nov 2017 by Codehead
7 minute read
After completing the video lectures of the Security Tube Linux 64 bit Assembler Expert course (SLAE64), a series of assessments must be completed to gain certification. This is the forth assignment; create a custom encoder/decoder to disguise a shellcode payload.
Many security and threat monitoring tools rely on signature matching to identify bad code. A good way to avoid signature based detection is to obscure the content of a payload with encryption or encoding. The same payload can be repeatedly disguised with different obfuscation schemes. Creating a new encoding method is much simpler than building a new payload.
For the assignment, we will design a simple encoding scheme, create an encoding script to disguise our shellcode and write a decoder stub which we will deploy with the payload to rebuild the original code on the fly.
Posted: 6 Nov 2017 by Codehead
10 minute read
After completing the video lectures of the Security Tube Linux 64 bit Assembler Expert course (SLAE64), a series of assessments must be completed to gain certification. This is the third assignment; research and create an egg hunter proof of concept.
Egg hunting is a technique which can be used to solve shellcode space restriction problems. The egg hunter is a very small piece of code that searches the process memory for an ‘egg’; a signature consisting of a known sequence of bytes. This signature is used to mark the start of the real payload, which could be much larger. Once the signature is located, the instruction pointer is redirected to the new location and the larger payload is executed.
Posted: 27 Oct 2017 by Codehead
12 minute read
After completing the video lectures of the Security Tube Linux 64 bit Assembler Expert course (SLAE64), a series of assessments must be completed to gain certification. This write up is for the second assignment: Create a shellcode string that will start a TCP Reverse Shell.
A reverse shell connects to a remote host on a given network address and port. Any commands issued by the remote host are relayed to a local shell on the target in the same way as the bind shell.
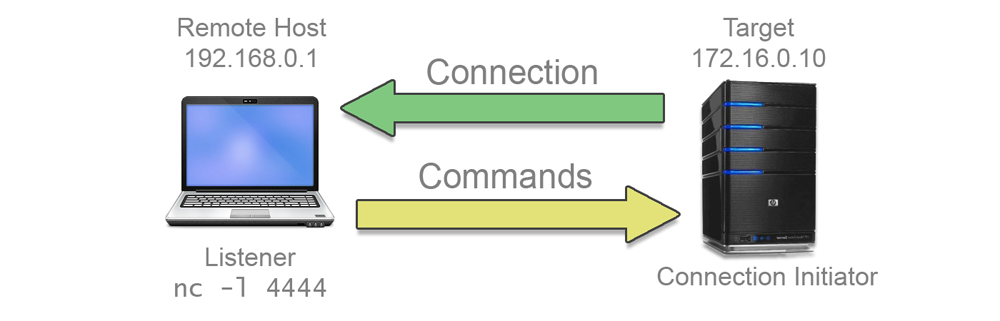
Having the target reach out to the remote machine may seem like an odd way of making the connection, especially as the remote must be ready and listening for the connection to be successful. However, this type of connection is preferable if the target is behind a firewall or a network address translation (NAT) layer which would make an inbound connection to a bind shell difficult.
As with the bind shell a passphrase must be implemented to add a layer of security to the program.
Posted: 23 Oct 2017 by Codehead
21 minute read
After completing the video lectures of the Security Tube Linux 64 bit Assembler Expert course (SLAE64), a series of assessments must be completed to gain certification. The first assignment is to create a shellcode string that will start a TCP Bind Shell.
A bind shell listens on a network port and waits for an incoming connection. When a connection is received, a new socket is created, the I/O streams of the host are cloned into this new socket and a new shell instance is spawned.
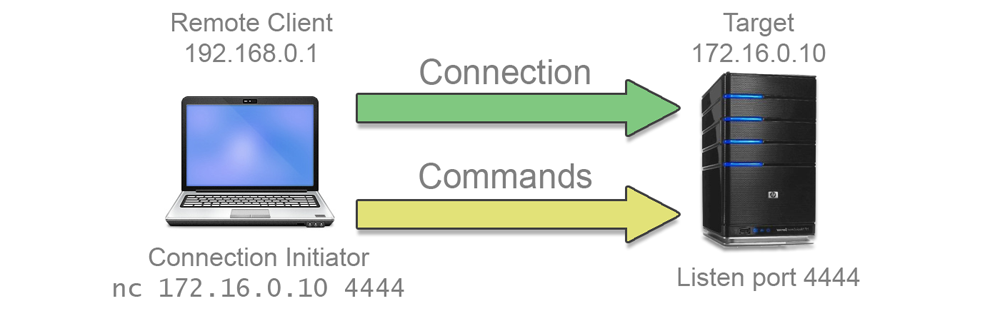
This has the effect of giving the remote user an interactive shell on the host system. Of course this is not as secure as something like an SSH connection, but is quite sufficient to let a remote user poke around the host system, issue commands and exfiltrate data.
As an extra twist, the assignment requires a little more security; a passphrase must be implemented in the bind shell code to prevent anyone who happens to stumble across the listening socket from simply dropping into the host shell.
Of course, this ‘security’ is limited and anyone eavesdropping on the connection could sniff the passphrase with minimal effort, but it is an interesting exercise.
Posted: 8 Oct 2017 by Codehead
2 minute read
A pretty simple crypto challenge, but the technique is applicable to more complex problems.
Challenge
The smart home system has the function of remote monitoring of what is happening in the home and every few minutes sends pictures of the surveillance cameras to the owner of the house. You successfully intercepted the network traffic of this system, however, its creators took care of the security of their users data and encrypted the pictures. Decrypt the provided image and you will find the flag.
SECRET_ENCRYPTED.PNG
Posted: 8 Oct 2017 by Codehead
5 minute read
The lowest scoring challenge at Kaspersky’s 2017 CTF turned out to be a pretty tricky. Mainly due to weird flag formatting, but also because I am stupid and couldn’t see a blatant clue staring me in the face.
Challenge
Hey! Do you like playing? Are you old school?
Have fun!
Concat answer to KLCTF prefix
OLD_SCHOOL.BIN
Posted: 20 Sep 2017 by Codehead
3 minute read
I was expecting a keygen or licence key cracking based on the title of this challenge, so revisiting some old protocols that I haven’t used in anger for ages was a nice surprise. The challenge blurb was pretty minimal:
Challenge
Serial
nc misc.chal.csaw.io 4239
Posted: 5 Sep 2016 by Codehead
2 minute read
I almost missed the Tokyo Westerns CTF. I stumbled across the event on the last day and wasn’t able to spend too long on it. I managed a few of challenges, mainly the PPC category. However, I wanted to write up the ‘Glance’ image manipulation challenge for future reference.
Challenge
I saw this through a gap of the door on a train.
Posted: 29 Aug 2016 by Codehead
3 minute read
Here’s a nice little 10 point binary challenge from CTF(x) 2016.
We’re told of a vulnerable service running at problems.ctfx.io 1338. We’re also given the source code:

