2 minute read
Challenge:
FlagStore (exp70)
Description:
Here’s the ultimate flag store. Store and retrieve your flags whenever you want.
FlagStore (exp70)
Here’s the ultimate flag store. Store and retrieve your flags whenever you want.
It’s Prime Time! (code60)
Description: We all know that prime numbers are quite important in cryptography. Can you help me to find some?
Service: 188.166.133.53:11059
Running netcat against the address gave the following output:
> nc 188.166.133.53 11059 Hi, you know that prime numbers are important, don't you? Help me calculating the next prime! Level 1.: Find the next prime number after 5:
I haven’t done much work with Ruby, but this little challenge from the Internetwache CTF looked interesting.
Ruby’s count (exp50)
Description: Hi, my name is Ruby. I like converting characters into ascii values and then calculating the sum.
Service: 188.166.133.53:12037
The first thing to do was to poke the service using netcat:
> nc 188.166.133.53 12037
Let me count the ascii values of 10 characters:
> 123
WRONG!!!! Only 10 characters matching /^[a-f]{10}$/ !
I hadn’t played SharifCTF before, but these guys put on a good competition.
Unfortunately I had other commitments, but I managed to spend a little bit of time looking at some of the challenges.
dMd was a reverse engineering challenge worth 50 points. A binary was provided with the description:
Flag is : The valid input.
file told me that the binary was an x86-64 ELF, so I threw it at my Fedora install and pulled up the disassembly in IDA.
SRM was another 50 point reverse engineering challenge at SharifCTF 2016. A binary was provided with the following description:
The flag is : The valid serial number.
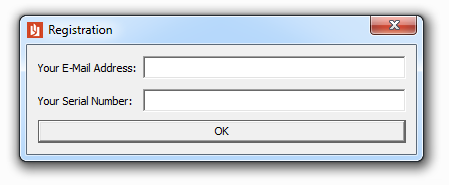
file reported that the binary was a PE32 for Windows. So I fired up a Win7 VM and pulled up the disassembly in IDA.
Running the binary resulted in a dialog asking for an email address and a serial number.
A nice little Stego challenge from SharifCTF
We have hidden a message in png file using jar file. Flag is hidden message. Flag is in this format:
SharifCTF{flag}
Extracting the supplied tar.gz archive provided a PNG image:

Also included was Hide.jar, the Java code used to embed the flag in the image.
Due to work commitments, I didn’t get to spend too much time on this CTF which was a shame because they put out some nice challenges. Here are the ones I did get to have a crack at: