Posted: 21 Feb 2016 by Codehead
2 minute read
I haven’t done much work with Ruby, but this little challenge from the Internetwache CTF looked interesting.
Challenge:
Ruby’s count (exp50)
Description: Hi, my name is Ruby. I like converting characters into ascii values and then calculating the sum.
Service: 188.166.133.53:12037
Solution
The first thing to do was to poke the service using netcat:
> nc 188.166.133.53 12037
Let me count the ascii values of 10 characters:
> 123
WRONG!!!! Only 10 characters matching /^[a-f]{10}$/ !
Posted: 7 Feb 2016 by Codehead
3 minute read
I hadn’t played SharifCTF before, but these guys put on a good competition.
Unfortunately I had other commitments, but I managed to spend a little bit of time looking at some of the challenges.
dMd was a reverse engineering challenge worth 50 points. A binary was provided with the description:
Flag is : The valid input.
file told me that the binary was an x86-64 ELF, so I threw it at my Fedora install and pulled up the disassembly in IDA.
Posted: 7 Feb 2016 by Codehead
2 minute read
SRM was another 50 point reverse engineering challenge at SharifCTF 2016. A binary was provided with the following description:
The flag is : The valid serial number.
file reported that the binary was a PE32 for Windows. So I fired up a Win7 VM and pulled up the disassembly in IDA.
Running the binary resulted in a dialog asking for an email address and a serial number.
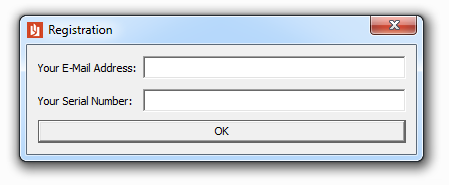
Posted: 7 Feb 2016 by Codehead
3 minute read
A nice little Stego challenge from SharifCTF
Challenge:
We have hidden a message in png file using jar file. Flag is hidden message. Flag is in this format:
SharifCTF{flag}
Files:
cheetah.tar.gz
Extracting the supplied tar.gz archive provided a PNG image:

Also included was Hide.jar, the Java code used to embed the flag in the image.
Posted: 26 Oct 2015 by Codehead
2 minute read
Due to work commitments, I didn’t get to spend too much time on this CTF which was a shame because they put out some nice challenges. Here are the ones I did get to have a crack at:
Posted: 26 Oct 2015 by Codehead
1 minute read
A faithful replica of a typical 90s webpage, complete with a searing neon colour scheme and Netscape buttons. Browsing the site, I noticed from the URL that the pages were being served through the main index.php script with a ‘page’ parameter. Lets change that page parameter to something we’d like to see: Ping! 20 points.

